Vulnerability Management: The Cornerstone of IT Security?!
Today, IT security is one of the most critical areas of business processes. The continuous rise of digitisation, the widespread use of cloud-based services and the development of increasingly complex systems have made it clear that IT security is not only a technological issue but also a matter of complex processes and appropriate planning. One of the fundamental pillars of this is vulnerability management, which is essential for the proper operation and maintenance of IT security processes.
What is Vulnerability Management?
Vulnerability management is a process by which an organisation identifies, prioritises and manages vulnerabilities that threaten the security of its systems and networks. This is not just a one-time task but an ongoing activity that takes into account changes in systems, software and networks, and ensures that any new vulnerabilities are dealt with quickly and efficiently.
Why is Vulnerability Management Important?
- Proactive protection: Vulnerability management enables organisations to proactively identify and address potential security vulnerabilities before they become a real threat. Instead of reacting only after attacks, companies can prevent problems.
- Cost efficiency: Preventing security incidents is much cheaper than recovering from attacks and dealing with the legal consequences. Regular vulnerability management minimises the chance of serious risks.
- Compliance with relevant regulations: Many industry standards and legal provisions (e.g. GDPR, PCI-DSS) require regular identification and management of vulnerabilities. Lack of vulnerability management can lead to fines and legal consequences.
- Maintaining business processes: A well-functioning vulnerability management process ensures business continuity, minimising the risk of system downtime and data loss.
The Solution is not Enough: The Importance of Processes
Many believe that choosing the right IT security solutions is enough to deal with vulnerabilities. Although it is really important to use the right tools and technologies, the key to the success of vulnerability management lies in the coordinated work of processes and people.
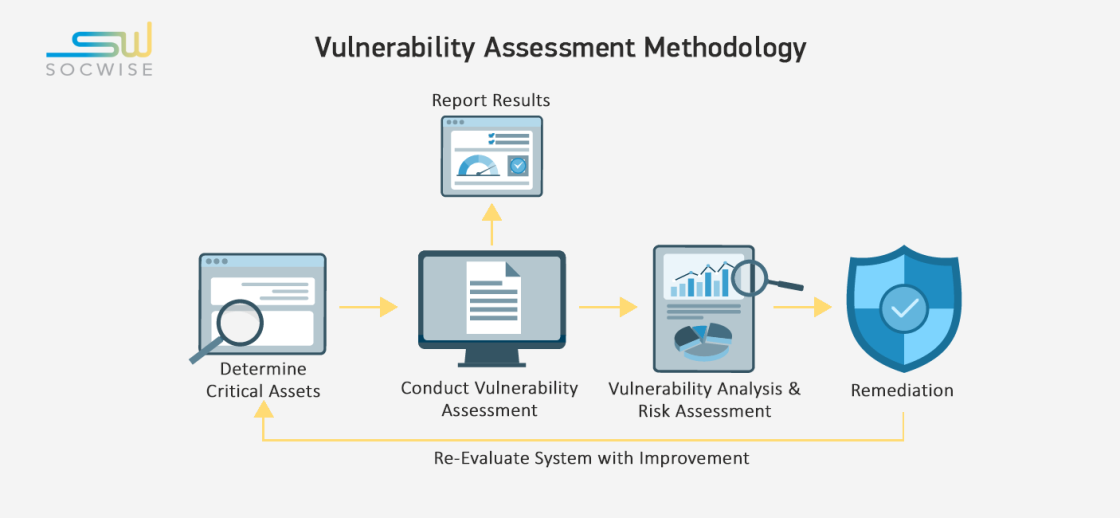
Development of processes
Vulnerability management cannot be effective without properly designed and regulated processes. A well-designed process should include all steps from identification and risk assessment to remediation and follow-up. Processes must be flexible to adapt to changing threats and technologies.
Change management and testing
One of the key elements of vulnerability management is change management, which ensures that all system and software updates and new installations are properly tested and evaluated from the viewpoint of security. The importance of testing is outstanding: vulnerabilities can only be discovered with regular, systematic testing before they can be exploited.
Human labour and expertise
In addition to automated solutions, there is also a need for people with the right expertise who can interpret the results, prioritise the risks and make decisions about the appropriate measures. People play a key role in ensuring that processes are not just based on technical solutions but become real, comprehensive protection.
Process development: a constant challenge
Vulnerability management is a constantly developing field, where technological innovations and increasingly sophisticated attack methods constantly present new challenges to organisations. Companies must focus not only on the management of current vulnerabilities but also on the continuous development of processes.
- Regular review: Processes must be regularly reviewed to ensure that they always meet the latest security requirements and threats.
- Training and awareness: Continuous training and awareness raising are essential for effective vulnerability management. Employees must be aware of the latest threats and procedures.
- Development and innovation: In the field of vulnerability management, one must always be open to new solutions, technologies and process developments.
Vulnerability management is an essential part of IT security processes, which ensures the security of systems, software and networks in a constantly changing environment. Although the selection of appropriate solutions is of fundamental importance, vulnerability management cannot be comprehensive without the development of processes, change management, regular testing and the integration of human work. The key to success lies in the coordinated operation of technology, processes and expertise, which guarantees the smooth and safe operation of business processes.


