The Zero Trust approach: Why is protection against internal threats becoming more important?
The world of cybersecurity is constantly changing and evolving as threats grow more sophisticated. For today's organizations it is no longer enough to defend against external attacks; defense against internal threats is also becoming more and more necessary. The "Zero Trust" approach is getting more and more popular in this context as it offers an effective solution for protection against internal and external threats.
What is the Zero Trust approach?
The essence of the Zero Trust approach is that no user or device is automatically trusted, regardless of whether it is inside or outside the network. This means that all access requests, whether from internal or external sources, must be thoroughly checked before granting access to corporate resources.
Why is protection against internal threats important?
Internal threats – whether it's malicious employees, careless mistakes or a compromised internal device – pose a serious risk to organisations. These threats are more difficult to detect and stop than external attacks because they often originate from internal company systems.
The Zero Trust approach aims to minimise the risks from internal threats by checking each access request and ensuring that only people with appropriate authorisation can access sensitive information.
The relationship between the NIS2 directive and the Zero Trust approach

The NIS2 directives of the European Union define binding rules for organizations operating critical infrastructures in the field of cybersecurity. NIS2 aims to improve organizations’ resilience to cyber threats and ensure that they are able to respond quickly and effectively to incidents.
NIS2 directives cover a number of areas including risk management, incident response, continuous monitoring and reporting. These requirements are clearly in line with the principles of the Zero Trust approach, which aims to continuously check and secure all accesses and activities.
The Palo Alto Networks and the Zero Trust approach
A strong and comprehensive cybersecurity strategy that includes the protection of all network and cloud-based resources is essential for successfully implementing the Zero Trust approach. The Palo Alto Networks play a leading role in this area with solutions that help organisations establish and maintain the Zero Trust architecture.
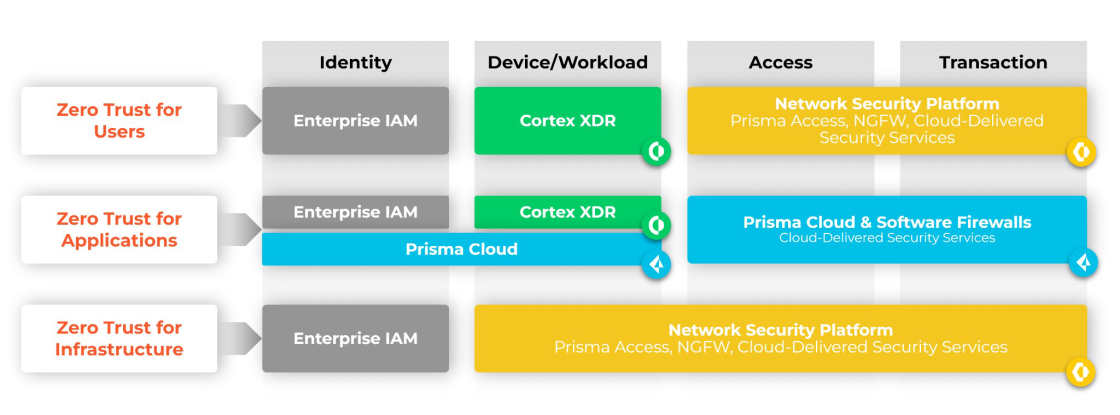
1. Prisma Access and Prisma Cloud
The Palo Alto Networks' Prisma Access and Prisma Cloud solutions enable organizations to securely manage traffic in cloud and hybrid environments. These solutions enable continuous verification, identification and authentication, which is fundamental to the Zero Trust approach. Continuous monitoring of user activities and real-time response ensure that any suspicious activity can be dealt with immediately.
2. Next-Generation Firewall (NGFW)
The Palo Alto Networks NGFW solutions have features such as dynamic user and device profiling, enabling access control based on the Zero Trust principles. NGFWs are capable of real-time threat detection and prevention while continuously monitoring network traffic in order to identify and block potential threats.
3. Cortex XSOAR
The Palo Alto Networks' Cortex XSOAR platform combines automation and intelligent incident management to help organizations respond faster and more effectively to internal and external threats. With the Zero Trust approach, Cortex XSOAR can identify suspicious activities and automatically initiate actions that are necessary to counter threats.
How to get started?
The implementation of the Zero Trust approach is not a one-time project but an ongoing process that requires comprehensive planning and continuous development. Organizations must first thoroughly assess their current cybersecurity posture and then identify the areas where implementing the Zero Trust approach can bring the greatest benefit.
The following steps are recommended in order to implement the Zero Trust approach:
- Identify critical resources and data: Determine which tools and data are most important to the organization and ensure that only authorized users can access them.
- Create a strong authentication and access management system: Use multi-factor authentication (MFA) and the strictest access control rules.
- Continuously monitor network traffic and user activities: Use tools like the Palo Alto Networks NGFW and Prisma solutions that provide real-time monitoring and response.
- Automate incident management: Implement automated systems like Cortex XSOAR to respond quickly and efficiently to emerging threats.
The Zero Trust approach is not just another security trend but a fundamental change in the way organizations manage cybersecurity. Protection against internal threats is no longer optional but a basic necessity, especially in an increasingly complex and globalized digital environment. With the help of solutions offered by the Palo Alto Networks, organizations can effectively defend themselves against both internal and external threats, thereby ensuring the security of corporate data and resources.


