What is Expected Today from the Main Incident Management Tools, SIEM and SOAR?
In IT security, cyber attacks are inevitable. Incident management is about responding efficiently to these threats, minimising damage and quickly restoring normal operations. SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) systems play a key role in this process.
Introduction to Incident Management
Incident management helps to detect, prevent and stop cyber attacks. A security incident could be, for example, a failed login attempt, a malware infection or a data theft. In IT, there are three terms that are sometimes used interchangeably but mean different things:
- Events: Harmless operations such as creating a file or opening an e-mail. An event on its own does not constitute a security incident, but when coupled with other events it may indicate a threat.
- Alerts: Notifications triggered by events that are either threats or not. On their own, no alert may appear to be a significant threat, but their combined presence may indicate a possible security incident.
- Incidents: A group of related alerts. Incident management seeks to contain a cyber-attack as quickly as possible, then perform the necessary restoration, notify management or supervisors in accordance with regional legislation, and, in the course of ongoing operations, the organisation learns how to reduce the risk of similar incidents occurring in the future.
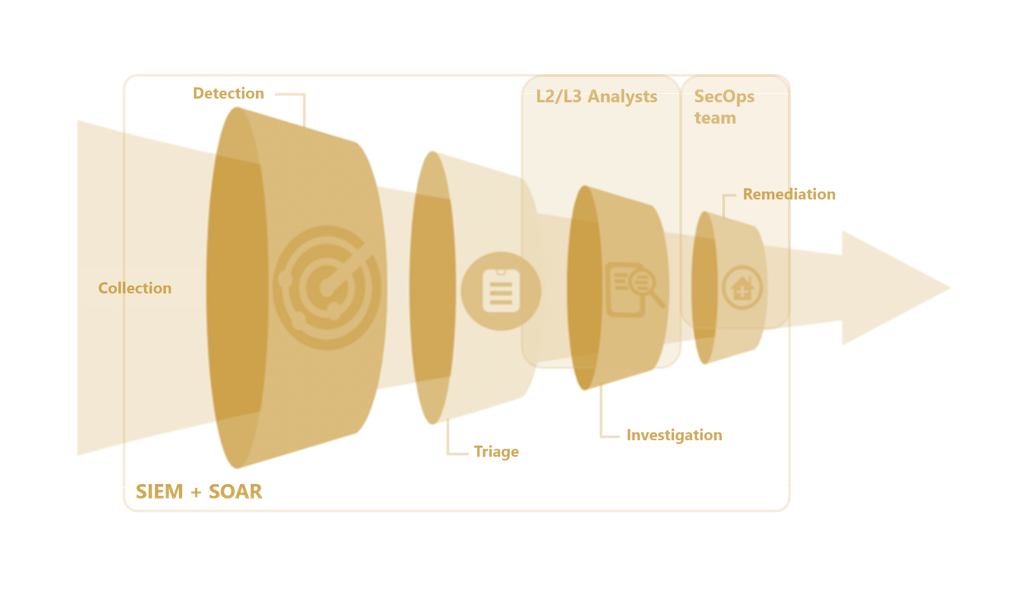
The Role of SIEM and SOAR Systems
SIEM (Security Information and Event Management) helps to store and process log information collected from applications, devices, networks and servers by identifying, categorising and analysing incidents and events. The SIEM system can collect multiple logs and generate alerts based on dynamic rules or machine learning. It uses correlation and context to identify complex attacks. It is also the main tool for analysts, as it is the only place where all relevant information is available in one system.
The SOAR (Security Orchestration, Automation, and Response) system enables the automation of manual processes and the management of alerts and incidents. The SOAR system connects different security tools and applications so that they can be managed in a unified way. Automated responses speed up incident response and minimise the possibility of human error.
SOAR Systems: Effective Incident Management Tools
Incident management is about responding efficiently to these threats, minimising damage and quickly restoring normal operations.
SOAR Systems
SOAR systems automate incident identification, incident analysis and the end-to-end incident management process. They not only automate the task of the analysts, but, for instance, ticket management as well. Their flexibility and adaptability are key to successful implementation.
- Cybersecurity Ticket Management: The SOAR system helps to manage tickets. It uses automated notifications and predefined processes to support users in responding to incidents in their specific roles.
- Workflow Customisation: Their flexibility allows workflow customisation. Processes can be tailored to the specific needs of the customer.
- Integrations: The SOAR system connects different security tools and applications. This makes system management uniform, minimising the possibility of human error. It’s called orchestration.
- Challenges: Although SOAR systems are efficient, not everything can be automated. For example, without the involvement of experts who are familiar with the network and systems in question, it is often not possible to fully implement incident management. Human interaction and expertise remain essential.
SIEM Systems
SIEM systems help to identify, categorise and analyse events and alerts. They can collect multiple logs and generate alerts based on machine learning. They can also use correlation and context to identify complex attacks. It is an important expectation that the logs should be stored for the long term.
Our partner’s Netwitness platform not only has log analysis capabilities, but also manages endpoint (EDR) and network (NDR, Full packet capture) data, as well as Machine Learning-based correlation capabilities (UEBA). Unlike SOAR systems, Netwitness is capable of basic incident management on its own.
About Us
Our team of experts has been in operation for 20 years and currently consists of 52 professionals, with the knowledge of our 5 Information Security Competence Centres supporting companies across Europe and in Hungary, including in meeting their NIS2 compliance needs. Our engineers assist in the implementation and operation of state-of-the-art technologies (SIEM, SOAR, XDR, MGFW, SASE, MFA, etc.). Our Cyber Defence consultants also perform penetration testing and Red Teaming, but their main task is to work with IT organisations to develop defence architectures and operational processes and integrate tools. And they have their own SOC team to monitor cyber security events.
Summary
SIEM systems help identify incidents and alarms, while SOAR systems automate incident management. Flexibility and adaptability are key requirements for effective implementation. And the Netwitness platform is a tool that manages endpoint and network data in addition to log analysis, and provides AI-based correlation capabilities. From meeting compliance needs to developing the security architecture and integrating tools, our expert teams can help you every step of the way to ensure security at the highest level


