Application of Cyber Security TTP Basic Principles in IT Security
The world of cybersecurity is facing ever-evolving threats, requiring organizations to stay up-to-date on attacks and defense strategies. One of the most important tools for understanding attackers and developing defense is the TTP (Tactics, Techniques and Procedures) framework. In this blog post, we introduce in details the principles of TTP and examine how they can be effectively applied to IT security.
What is TTP (Tactics, Techniques and Procedures)?
The TTP abbreviation stands for three components:
- Tactics: Common goals or strategies that attackers use to try to achieve their goals, such as obtaining information, disrupting systems or stealing data. Tactics determine what goals the attacker is fighting for and what direction the attack will take.
- Techniques: The specific methods or tools used to execute the tactics. These can be, for example, the exploitation of specific vulnerabilities, the use of social engineering techniques or the distribution of malicious codes.
- Procedures: The specific steps or actions that attackers follow when performing the techniques. These procedures describe in detail how attackers carry out their attacks, including tools, scripts and steps of the attack.
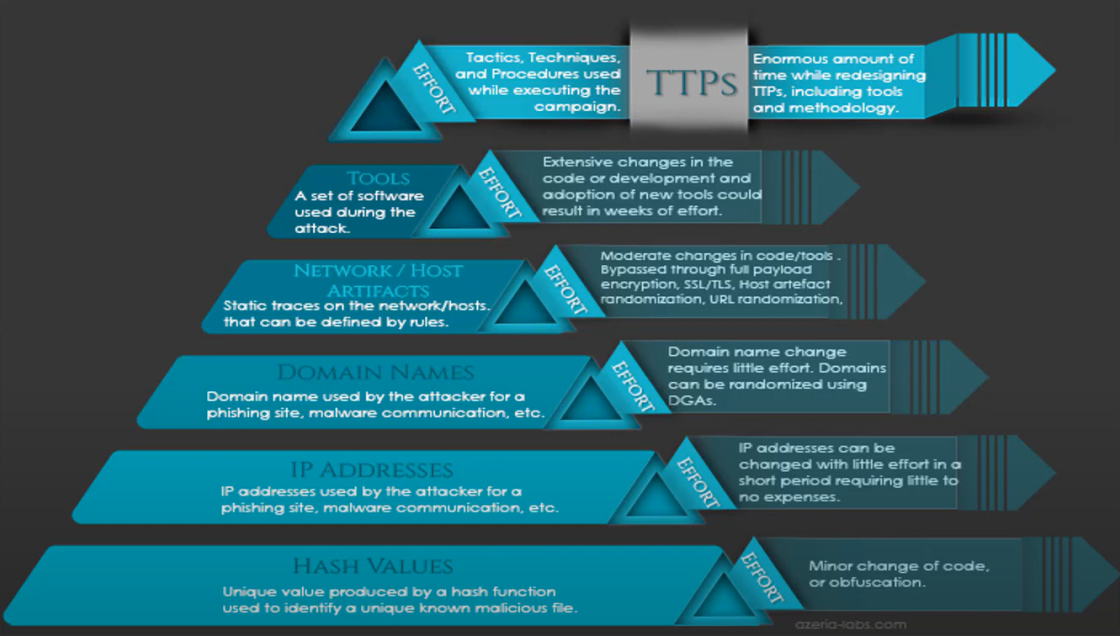
Why is it important to use TTP in IT security?
Tactics: Identifying attack targets
It is essential for IT security professionals to understand the tactics of attackers. This helps them identify what targets attackers are focusing on and what strategies they use to reach them. For example, an attacker may aim to gain access to a system, leak confidential data or perform denial-of-service (DoS) attacks. Tactical-level analysis helps design defense strategies to minimize the success of attacks.
Techniques: Recognizing specific attack methods
Knowing the techniques used by attackers allows organizations to develop specific defense measures. For example, if an attacker uses social engineering techniques, the organization can increase employee training and awareness of these types of threats. Similarly, when attackers exploit known vulnerabilities, regular patch management and vulnerability management become crucial.
Procedures: Understanding and preventing attack processes
Through process analysis, defense teams can understand how attackers execute their attacks, so they can tailor defense strategies accordingly. Such information allows threat detection systems to be fine-tuned to detect suspicious activities. For example, if an attacker follows known procedures in a network attack, the defense team can pre-configure intrusion detection systems to respond immediately to such activities.
Integrating TTP-based protection
Incorporating a TTP-based approach into the IT security strategy enables proactive defense. A detailed understanding of TTPs helps organizations anticipate attack patterns and prepare to defend accordingly. This includes improving threat detection, increasing the effectiveness of incident response and continuously improving cyber security measures.
Closing thoughts
A thorough understanding and application of TTP principles is crucial in today's IT security environment. Attackers are constantly evolving and developing new techniques and procedures to achieve their goals. Understanding TTPs allows organizations to anticipate and more effectively prevent these attacks. Such a comprehensive approach to cyber security increases the effectiveness of protection and the security of the organization.


